Warning: Critical Vulnerability CVE-2025-31702 in Dahua Devices and How to Fix It
A severe security vulnerability has recently been discovered in numerous product lines of cameras and network video recorders (NVRs) from Dahua, one of the world’s most popular surveillance equipment brands. This flaw, identified as CVE-2025-31702, could allow an attacker to gain complete administrative control of a device without needing the original password.
This is an extremely dangerous issue that could expose the entire surveillance systems of homes and businesses to malicious actors, leading to data theft, espionage, or even complete system shutdown.
How Dangerous is the CVE-2025-31702 Vulnerability?
In simple terms, this vulnerability allows a person with low-level access (e.g., a “viewer” or “operator” account with a weak password) to escalate their privileges to become a full administrator (admin).
An attacker can achieve this by exploiting a flaw in the device’s password recovery mechanism. They can read a file containing a “secret code,” which then allows them to generate a recovery code and reset the admin account’s password.
Even more concerning, security researchers uncovered two accompanying issues:
- Insecure P2P Protocol: Older firmware versions allow connections to the device via the P2P protocol simply by knowing the serial number (S/N), with no password required. This means a hacker could remotely access your device even if you haven’t opened any ports on your router.
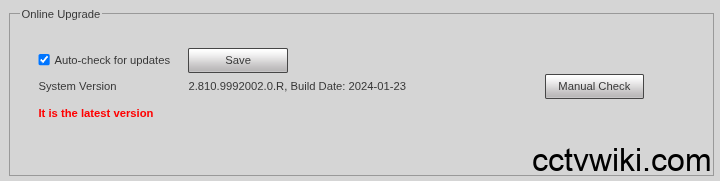
- Misleading “Auto-Update” Feature: The device’s web interface might report that it is “already on the latest version,” when in fact, a newer, patched firmware is available on Dahua’s official website. This creates a false sense of security, preventing users from applying critical security updates.
Which Dahua Devices Are Affected?
According to Dahua’s confirmation, the following product lines are affected by CVE-2025-31702:
- IPC-1XXX Series
- IPC-2XXX Series
- IPC-WX Series
- IPC-ECXX Series
- SD3A Series
- SD2A Series
- SD3D Series
- SDT2A Series
- SD2C Series
- TPC-AEBF5201 Series
- TPC-CA Series
Additionally, devices from Lorex and Tiandy may also be vulnerable due to similarities in their firmware and protocols.
How to Protect Your System?
To secure your surveillance system, you must take the following steps immediately:
- Disable P2P (Easy4IP) if Not Needed: This is the most crucial step. If you do not need to view your cameras remotely over the internet, navigate to Settings → Network → Access Platform and disable the P2P feature.
- Manually Update Firmware: Do not fully trust the auto-update feature. Visit Dahua’s official website, search for your device model, and download the latest firmware version to update it manually.
- Use Strong, Unique Passwords: Set complex passwords for all accounts, including the administrator and any secondary user accounts. Delete any unused accounts.
- Segment Your Network and Use a VPN: For business environments, it is highly recommended to isolate the surveillance system on a separate VLAN. Use a VPN for remote access and block outbound P2P connections at the firewall.
- Monitor for Unusual Activity: Regularly check the device logs for suspicious signs, such as password changes, user privilege modifications, or strange P2P connections (especially logins from the address 127.0.0.1).
By taking these proactive measures, you can effectively protect your surveillance system from the risks posed by the CVE-2025-31702 vulnerability and ensure the safety of your personal data and property.

