The majority of the recent camera product ranges of Hikvision cameras are susceptible to a critical remote unauthenticated code execution vulnerability even with latest firmware (as of 21 June 2021). Some older models are affected also as far back as at least 2016. Some NVRs are also affected, though this is less widespread.
This is being tracked as CVE-2021-36260
Hikvision’s security advisory: security-notification-command-injection-vulnerability-in-some-hikvision-products
Summary
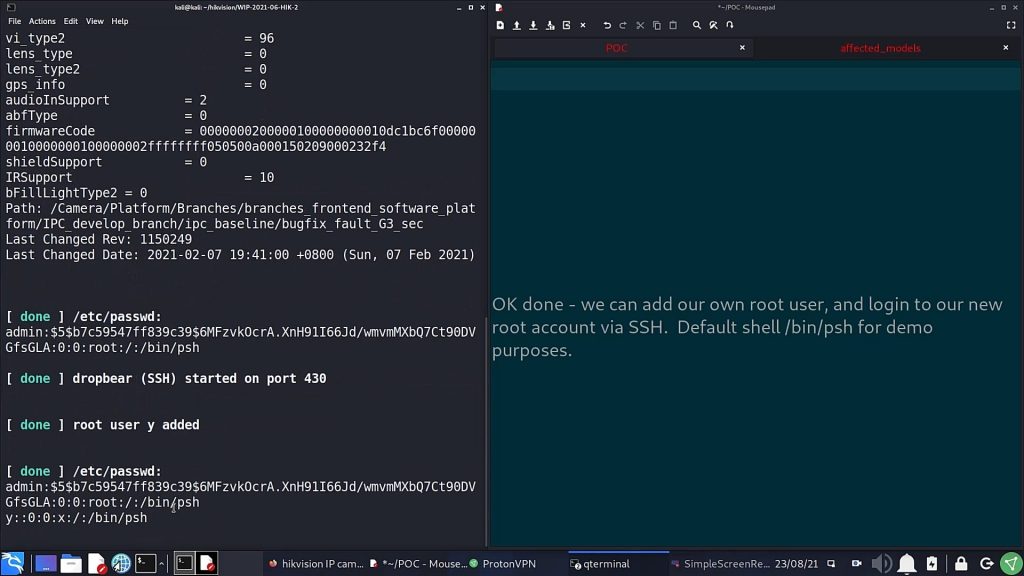
This permits an attacker to gain full control of device with an unrestricted root shell, which is far more access than even the owner of the device has as they are restricted to a limited “protected shell” (psh) which filters input to a predefined set of limited, mostly informational commands.
In addition to complete compromise of the IP camera, internal networks can then be accessed and attacked.
This is the highest level of critical vulnerability – a zero click unauthenticated remote code execution (RCE) vulnerability affecting a high number of Hikvision cameras. Connected internal networks at risk
Given the deployment of these cameras at sensitive sites potentially even critical infrastructure is at risk.
A list of affected firmware types can be found at the end of this document.
Firmware from as long ago as 2016 has been tested and found to be vulnerable.
Only access to the http(s) server port (typically 80/443) is needed. No username or password needed nor any actions need to be initiated by camera owner. It will not be detectable by any logging on the camera itself.
This vulnerability was reported to Hikvision the day after discovery, on 21 June 2021. I wrote a full report to them identifying the problem code, the device types affected, POC and recommendations for resolution.
At the time of writing, patched firmware is partially available though inconsistently deployed across various Hikvision firmware portals.
CVE-2021-36260
CVE-2021-36260 POC command injection vulnerability in the web server of some Hikvision product. Due to the insufficient input validation, attacker can exploit the vulnerability to launch a command injection attack by sending some messages with malicious commands.
Exploit Title: Hikvision Web Server Build 210702 – Command Injection
Exploit Author: bashis
Vendor Homepage: https://www.hikvision.com/
Version: 1.0
CVE: CVE-2021-36260
Reference: https://watchfulip.github.io/2021/09/18/Hikvision-IP-Camera-Unauthenticated-RCE.html
All credit to Watchful_IP
Note:
- This code will not verify if remote is Hikvision device or not.
- Most of my interest in this code has been concentrated on how to reliably detect vulnerable and/or exploitable devices. Some devices are easy to detect, verify and exploit the vulnerability, other devices may be vulnerable but not so easy to verify and exploit. I think the combined verification code should have very high accuracy.
- ‘safe check’ (–check) will try write and read for verification ‘unsafe check’ (–reboot) will try reboot the device for verification
Safe and unsafe vulnerability/verify check: (will only use ‘unsafe check’ if not verified with ‘safe check’) $./CVE-2021-36260.py –rhost 192.168.57.20 –rport 8080 –check –reboot
Unsafe vulnerability/verify check: $./CVE-2021-36260.py –rhost 192.168.57.20 –rport 8080 –reboot
Launch and connect to SSH shell: $./CVE-2021-36260.py –rhost 192.168.57.20 –rport 8080 –shell
Execute command: $./CVE-2021-36260.py –rhost 192.168.57.20 –rport 8080 –cmd “ls -l”
Execute blind command: $./CVE-2021-36260.py –rhost 192.168.57.20 –rport 8080 –cmd_blind “reboot”